While NSCIDs and DoD Directives offer general
guidance on the activities of NSA and the United States SIGINT System (USSS), far more detailed guidance is provided by the director of NSA in the form of United States Signals Intelligence Directives (USSIDs). The directives fall into at least nine different categories: policy, collection, processing, analysis and reporting, standards, administration, training, data processing, and tasking.
In the aftermath of revelations in the 1970s about NSA interception of the communications of anti-war and other political activists new procedures were established governing the interception of communications involving Americans.5 The version of USSID 18 currently in force was issued in July 1993 and "prescribes policies and procedures and assigns responsibilities to ensure that the
missions and functions of the United States SIGINT System (USSS) are conducted in a manner that safeguards the constitutional rights of U.S. persons."
Section 4 ("Collection," pp.2-6) specifies the circumstances under which U.S. SIGINT activities may intercept communications of or about U.S. persons, as well as the authorities of the Foreign Intelligence Surveillance Court, the Attorney General, and the Director of NSA to approve the collection of such information.
Section 5 ("Processing," pp.6-7)
focuses on the restrictions on processing intercepted communications involving U.S. persons--including domestic communications collected during foreign communications collection operations.
Section 6 ("Retention," p.8) deals with the retention of intercepted communications about U.S. persons. Section 7 ("Dissemination," pp.8-10) concerns restrictions on dissemination. It requires that all SIGINT reports be written "so as to focus solely on the activities of foreign entities and persons and their agents." It also specifies some of the conditions under which U.S. persons can be identified in SIGINT reports--for example, when the communications indicate the person is an agent of a foreign power.
Document 7a. NSA, "USSID
18: Dissemination of U.S. Government Organizations and Officials (U)--INFORMATION
MEMORANDUM," February 5, 1993.
This NSA memo indicates that the conditions for identification
of U.S. officials by title in NSA reporting varies depending on whether
or not the individual is a member of the executive branch. Senior officials of the executive branch may be identified by title, without prior approval from higher authority, when the official's title is necessary to understand or assess foreign intelligence. In contrast, officials from the legislative and judicial branches cannot be identified by title, even if that information is necessary to understand foreign intelligence, unless approval is obtained from higher authority. The memo implies that, under the assumed conditions, the use of names is not permitted.
Document 7b. NSA, "USSID 18: Reporting Guidance on References to the First Lady," July 8, 1993.
This memo followed a U.S. Court of Appeals ruling that Hillary Clinton was a full-time government official. It notes that she could be identified in reports by title (Chairperson of the President's Task Force on National Health Care Reform) without prior approval when that title was necessary to understand or assess foreign intelligence and when the information related to her official duties. The memo also contains guidance on reports containing information about information concerning Mrs. Clinton that is not clearly foreign intelligence.
Document 7c. National Security Agency/Central Security Service, "U.S. Identities in SIGINT," March 1994.
This 48-page document is intended to provide detailed
guidance concerning on the use of U.S. identities in SIGINT reports as
well as the dissemination of U.S. identities to consumers outside the United States SIGINT System. It consists of 12 sections (including ones on requests for U.S. identities, accountability, dissemination, and collection and processing), and five appendices (including those on approved generic references and USSID 18 criteria for dissemination).
Document No. 7d. NSA, USSID 18: Reporting Guidance on Former President Carter's Involvement in the Bosnian Peace Process (U)-- Information Guidance, December 15, 1994.
The issue of when the identity or even title of a U.S. citizen can be included in reporting based on communications intercepts is a major focus of USSID 18. This NSA memo was prepared in response to the invitation to former President Carter to travel to Bosnia and Herzegovina to participate in efforts to end the war. It specifies that as long as Carter is acting as a private citizen he may be referred to only as a "U.S. person" in any reports.
Document 7e. NSA, "Understanding USSID
18 and Contextual Identifications," September 30, 1997.
The issue of identification by context is the subject of this memo. It notes that, in describing U.S. entities, analysts are required, in general, to substitute sufficiently generic terms for the entities--terms that do not "directly lead to the identification of a U.S. entity even though the identity has been obscured in the report." Violation of the "contextual identification rule" requires that the report "must be cancelled, reworded and reissued to eliminate the identifying information."
The guidance clearly does not apply to those cases where inclusion of more specific information is necessary to evaluate foreign intelligence.
Document No. 7f, NSA, "USSID 18 Guide," February 1998.
The introduction to this document notes that it is an informal guide to the provisions of USSID 18 with respect to the issue of the COMINT collection and and dissemination of U.S. identities.
One section focues on USSID 18 issues with respect to threat situations,
including when an individual is held captive by a foreign power or group or when an intercept reveals a threat to a U.S. person. The section on non-threat situations contains guidance on the disposition of the inadvertent intercept of communciations between U.S. persons, on processing and reporting of incidentally intercepted ommunications of a U.S. person during foreign intelligence collection, and the handling of U.S. identities in reports.
Document
8. Director of Central Intelligence Directive (DCID) 6/1, "SIGINT
Committee," May 12, 1982.
The SIGINT Committee, now known as the National SIGINT Committee, was first established in 1958 to oversee key aspects of U.S. SIGINT activities—the identification of collection requirements, evaluation of how well U.S. and allied SIGINT activities satisfy requirements, and the production of recommendations concerning SIGINT arrangements with foreign governments. This directive is the most recent available version of DCID 6/1. While the directive remains formally classified, the full text of the document has been published previously in scholarly works and on the world wide web.6
The SIGINT Committee operated for many years with
two permanent subcommittees—the SIGINT Requirements Validation and Evaluation Subcommittee (SIRVES) and the SIGINT Overhead Reconnaissance Subcommittee (SORS). In the mid-1990s two new groups were established: The Weapons and Space Systems Advisory Group, to "coordinate SIGINT on foreign weapons and space systems," and the National Emitter Intelligence Subcommittee, which focuses on SIGINT production concerning foreign radars and other non-communications signals.7
Document
9. NAVSECGRU Instruction C5450.48A, Subj: Mission, Functions and
Tasks of Naval Security Group Activity (NAVSECGRUACT) Sugar Grove, West
Virginia, September 3, 1991.
While NSA directs and manages U.S. SIGINT activities,
almost all collection activity is actually carried out by the military
service SIGINT units—including the Naval Security Group Command. The role of the unit at Sugar Grove in intercepting the international leased carrier (ILC) communications passing through INTELSAT satellites was first revealed in James Bamford's The Puzzle Palace8
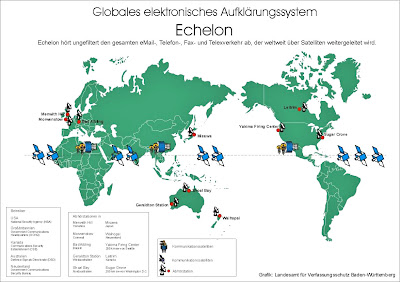
The regulation reveals that Sugar Grove is associated with what has become a highly controversial program in Europe, North America, Australia, and New Zealand. The program, codenamed ECHELON, has been described as a global surveillance network that intercepts and processes the world's communications and distributes it among the primary partners in the decades-old UKUSA alliance—the United States, Canada, the United Kingdom, Australia, and New Zealand.9
In reality, ECHELON is a more limited program, allowing
the UKUSA allies to specify intelligence requirements and automatically receive relevant intercepts obtained by the UKUSA facilities which intercept satellite communications (but not the U.S. facilities that receive data from SIGINT satellites). It is also limited by both technological barriers (the inability to develop word-spotting software so as to allow for the automatic processing of intercepted conversations) and the limitations imposed on collection activities by the UKUSA allies—at least as regards the citizens of those countries.10
Thus, the NAVSECGRU instruction also specifies that one of the responsibilities of the commander of the Sugar Grove site is to "ensure the privacy of U.S.
citizens are properly safeguarded pursuant to the provisions of USSID 18."
Document
10. Farewell from Vice Admiral William O. Studeman to NSA Employees,
April 8, 1992.
This address by the departing director of NSA, William
Studeman, examines NSA's post-Cold War mission, likely budgetary limitations, and other challenges facing the agency. Reflecting the increasing emphasis on "support to military operations," Studeman notes that "the military account is basic to NSA as a defense agency, and the lack of utter faithfulness to this fact will court decline." He also observes that "the demands for increased global access are growing" and that "these business areas (SMO and global access) will be the two, hopefully strong legs on which NSA must stand." He also argues that "technical and operational innovation to deal with a changing and changed world must continue to dominate."
Document
11. Letter, Stewart A. Baker, General Counsel, NSA to Gerald E. McDowell,
Esq., September 9, 1992.
In the wake of disclosures about the role of the Banca Nazionale del Lavoro (BNL), particularly its Atlanta branch, in the provision of financial assistance to the regime of Saddam Hussein, questions were raised about whether the intelligence community was providing sufficient support to law enforcement.
This letter, from NSA's general counsel, answers a series of questions from the Justice Department pertaining to NSA's knowledge of, or involvement in, BNL activities. The responses appear to indicate that NSA had not derived any intelligence concerning BNL activities from its intercept operations. The letter also stresses NSA's sensitivity to the issue of the privacy of American citizens (noting that "NSA improperly targeted the communications of a number of Americans opposed to the Vietnam War") and the restrictions on reporting information concerning U.S. citizens or corporations.
Document
12. "Activation of Echelon Units," from History of the Air Intelligence
Agency, 1 January - 31 December 1994, Volume I (San Antonio, TX: AIA,
1995).
The first extract from the Air Intelligence Agency's 1994 annual history provides additional information on the ECHELON network. ECHELON units include components of the AIA's 544th Intelligence Group.
Detachment 2 and 3 are located at Sabana Seca, Puerto Rico and Sugar Grove, West Virginia respectively. The second reference to Detachment 3 is apparently a typo that should read Detachment 4 (located at Yakima, Washington). The deleted words appear to be "civilian communications," "NAVSECGRU" and "NSA."
The second extract notes that AIA’s participation in a classified activity "had been limited to LADYLOVE operations at Misawa AB [Air Base], Japan." The Misawa LADYLOVE activity was initiated during the Cold War to intercept Soviet military communications transmitted via satellite—along with similar operations at Menwith Hill, UK; Bad Aibling, Germany; and Rosman, North Carolina. This extract suggests that both Guam and Misawa have, at the least, been considered as possible sites for ECHELON operations.
Document
13. NSA Point Paper, "SIGINT Reporting on Murders of Michael DeVine
in 1990 and the Disappearance of Efraín Bamaca in 1992 in Guatemala,"
March 24, 1995.
On March 23, 1995, Rep. Robert Torricelli, a member
of the House Permanent Select Committee on Intelligence, charged that the CIA had been withholding from Congress information it had obtained regarding the deaths of Michael DeVine, an American innkeeper living in Guatemala, and Efraín Bámaca Velásquez, a Guatemalan guerrilla leader and husband of an American lawyer. Both murders, according to Torricelli, were linked to a Guatemalan army colonel, Julio Roberto Alpírez, a paid intelligence asset of the CIA.11
The revelations set off a firestorm of criticism and caused the Clinton administration to order a government-wide investigation over these and other cases of torture and murder attributed to Guatemalan security forces. While the CIA was the main target of such criticism, Torricelli had also reportedly received an anonymous fax from someone inside the NSA alleging that documents pertaining to the Bámaca and DeVine cases were being destroyed.
12
This Top Secret NSA position paper responds to these
allegations. NSA claims that SIGINT reporting related to these cases is
limited to "Guatemalan government reaction to U.S. and international human rights concerns," and does not include specific information regarding the circumstances of death or the involvement of Colonel Alpírez. The document is one of only a handful of declassified records in which the NSA even acknowledges specific SIGINT activities or reports.
Document
14. Memorandum, Daniel C. Kurtzer, Acting Assitant Secretary, Bureau of
Intelligence and Research to Vice Admiral J.M. McConnell, Director, National
Security Agency, Subject: Proposed Declassification of the "Fact of" Overhead
SIGINT Collection, September 6, 1995.
In 1978, President Jimmy Carter acknowledged that
the U.S. employed reconnaissance satellites to collect imagery of foreign targets. Early in 1995, President Clinton declassified details concerning early satellite imagery programs such as CORONA. However, even the existence of SIGINT satellites remained classified until late 1995 when Director of Central Intelligence John Deutch authorized the official acknowledgement of space-based SIGINT operations.
13
The process involved soliciting the opinions of U.S.
government departments whose interests might be affected by disclosure. The State Department's memo expressed concern about the impact in certain countries. Despite the deletions, it is clear that the department was anxious about the impact in the foreign countries where the U.S. operates ground stations for SIGINT satellites—the United Kingdom (at Menwith Hill), Germany (at Bad Aibling), and Australia (at Pine Gap). The memo also indicates that the proposal for declassification emanated from the National Reconnaissance
Office.
Document
15. Organization Chart, NSA Operations Directorate, November 4, 1998.
The organization chart of NSA's Directorate of Operations is notable for several reasons. Traditionally, such information was not released by NSA, which under the provisions of Public Law 86-36 is not required to release even unclassified organizational information. In recent years, however, NSA has released more information about organization and administrative matters, and acknowledged the use of a variety of aircraft for SIGINT collection.
The organization chart also shows how the operations directorate has been reorganized since the end of the Cold War. Throughout much of the Cold War, the directorate consisted of three key regional groups—A (Soviet Bloc), B (Asian Communist), and G (All Other). After the Soviet collapse the regional groups were reduced to one for European nations and one for all other. The new organizational structure reflects the increasing empahsis on transnational activities, which cut across nations and regions.
Document 16. Statement for the Record of NSA Director Lt Gen Michael V. Hayden, USAF before the House Permanent Select Committee on Intelligence, April 12, 2000.
In a rare public appearance by the NSA director, Lt. Gen. Michael Hayden outlines the regulatory safeguards and oversight mechanisms that are in place to ensure that the agency's electronic surveillance mission does not infringe upon the privacy of U.S. persons, and to respond to recent allegations that NSA provides intelligence information to U.S. companies.
The agency may only target the communications of U.S. persons within the United States after obtaining a federal court order suggesting that the individual might be "an agent of a foreign power."
The number of such cases have been "very few" since the passage of the
Foreign Intelligence Surveillance Act in 1978. In cases where the NSA wishes to conduct electronic surveillance on U.S. persons overseas, the agency must first obtain the approval of the Attorney General, who must have probable cause to believe that the individual "is an agent of a foreign power, or a spy, terrorist, saboteur, or someone who aides or abets them."
With regard to the unintentional collection of communications
to, from, or about U.S. citizens, Hayden stresses that such information
is not retained "unless the information is necessary to understand a particular piece of foreign intelligence or assess its importance."
In response to other allegations, Hayden asserts that NSA cannot request that another country "illegally" collect intelligence on U.S. persons on their behalf, and also that the agency "is not authorized to provide signals intelligence information to private U.S. companies."
Return
to Index of Electronic Briefing Books
Return to National
Security Archive Main Menu
Notes
3. National Security Agency, NSA/CSS Manual 22-1 (Ft.
Meade, Md.: NSA, 1986), p. 7.
4. Stansfield Turner, Secrecy and Democracy: The
CIA in Transition (Boston: Houghton-Mifflin, 1985), pp. 235-236.
5. Bob Woodward, "Messages of Activists Intercepted,"
Washington
Post, October 13, 1975, pp. A1, A14.
6. See Jeffrey T. Richelson, The U.S. Intelligence
Community (Cambridge: Ballinger, 2nd ed., 1989/Boulder: Westview Press,
3rd ed., 1995; 4th ed., 1999); See also the World Wide Web site of the
Federation of American Scientists, http://fas.org/irp/offdocs/dcid16.htm
7. Lois G. Brown, "National SIGINT Committee," NSA
Newsletter, February 1997, p. 2.
8. James Bamford, The Puzzle Palace: A Report on
NSA, America's Most Secret Agency (Boston, MA: Houghton-Mifflin, 1982),
p. 170.
9. Patrick S. Poole, ECHELON: America's Secret Global
Surveillance Network (Washington, D.C.: Free Congress Foundation, October
1998).
10. Duncan Campbell, Interception Capabilities 2000
(Luxembourg: European Parliament, 1999); Jeffrey
T. Richelson, "Desperately Seeking Signals," Bulletin of the Atomic
Scientists, Vol. 56, No. 2, pp. 47-51.
11. Dana Priest, “Torricelli Admits Violating House
Secrecy Oath,” Washington Post, April 8, 1995, p. A7.
12. Kim Masters, “Truth or Consequences; Rep. Bob Torricelli
Leaked the Goods on the CIA. Was It Loyalty or Betrayal?” Washington
Post, April 17, 1995, p. C1.
13. DIRNSA, "Fact of Overhead SIGINT Collection," January
4, 1996.






 See: John St. Clair Akwei VS NSA
See: John St. Clair Akwei VS NSA 

 NSA Remote Neural Monitoring Of The American People's Brains And The Concept Of Punishing People For Their Thoughts Has Become A Reality In The United States
NSA Remote Neural Monitoring Of The American People's Brains And The Concept Of Punishing People For Their Thoughts Has Become A Reality In The United States





























